I often get asked how well the FortiGates handle firmware upgrades when they're in a high availability cluster. Clients want to know how the upgrade is handled and if there's any 'gotchas' they should be aware of.
Great news is that for the last few years the HA firmware upgrades are very simple and automated. No more manually breaking, upgrading then rejoining the clustered units each time a firmware upgrade is required.
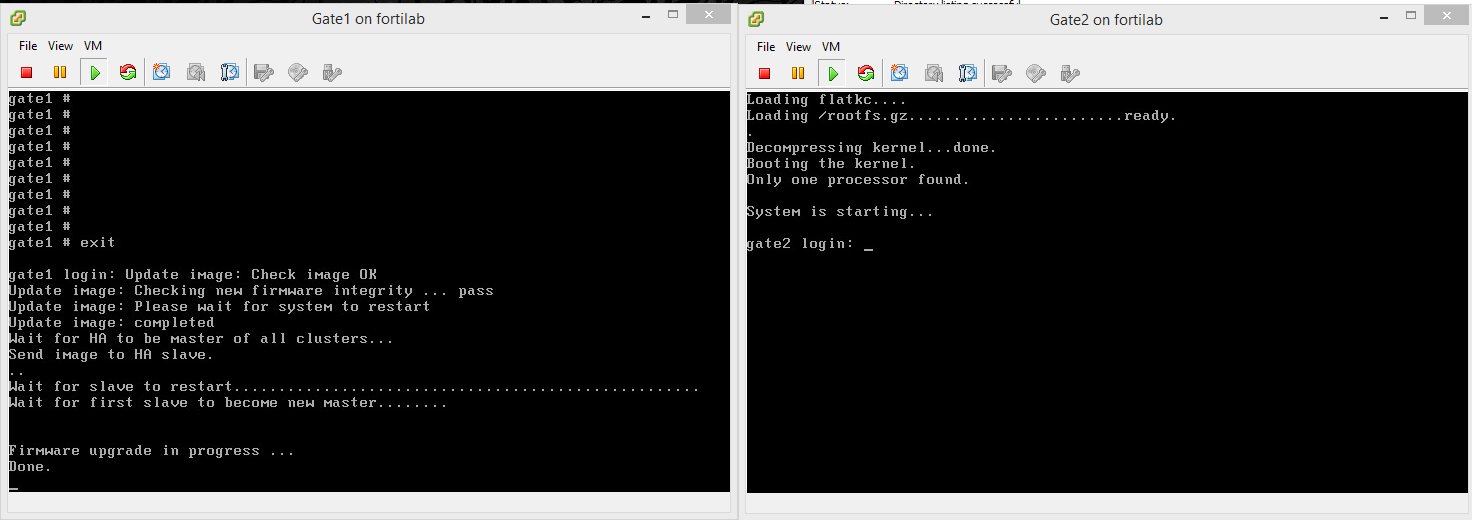
Below are the steps that occur during the upgrade process and I'll be referencing two devices, 'gate1' and 'gate2'. After each device I'll also define what rank they currently posses in the cluster (master or slave) at that point in time. When the upgrade first begins, gate1 is master and gate2 is slave.
1. Upload desired firmware to the cluster either via the webgui/CLI from the FortiGate or via a FortiManager
4. Gate2 (slave) upgrades it's firmware and reboots
One key thing I always point out is that all SSLVPN connections will be closed each time the master/slave handover happens. This means that remote users that have connected to the SSLVPN will be disconnected and can simply reconnect. This master/slave swap happens twice in the space of a few minutes, so they may be disconnected twice. All in all the upgrade takes about five minutes to complete.
Remember, as with all upgrades ensure that you have:
Great news is that for the last few years the HA firmware upgrades are very simple and automated. No more manually breaking, upgrading then rejoining the clustered units each time a firmware upgrade is required.
Below are the steps that occur during the upgrade process and I'll be referencing two devices, 'gate1' and 'gate2'. After each device I'll also define what rank they currently posses in the cluster (master or slave) at that point in time. When the upgrade first begins, gate1 is master and gate2 is slave.
1. Upload desired firmware to the cluster either via the webgui/CLI from the FortiGate or via a FortiManager
2. Once firmware has been uploaded gate1 (master) device will do a check sum and integrity check on the image to confirm it's good then send it off to gate2 (slave)
3. If the HA cluster is Active/Active then the load balancing is turned off, forcing all data to go through gate1 (master)
4. Gate2 (slave) upgrades it's firmware and reboots
5. Once gate2 (slave) has rebooted with the new firmware, it will inform gate1 (master) that the upgrade has been successful. Gate1 (master) will now demote itself to gate1 (slave), and gate2 (slave) will be promoted to gate2 (master). ***At this point in time, all SSLVPN connections will be terminated***
6. All traffic will now be routed through gate2 (master)
7. Gate1 (slave) will now upgrade it's firmware and reboot
8. Once gate1 (slave) has upgraded/rebooted, it will promote itself to gate1 (master), and demote gate2 (slave). ***At this point in time, all SSLVPN connections will be terminated***
9. All traffic is now being routed through gate1 (master) and the firmware upgrade has completed.
So in a nutshell, once you've started the upgrade process, the FortiGates will automatically upgrade and reboot each device in turn, and you'll end up with the original master as the final master when the upgrade has finished.
One key thing I always point out is that all SSLVPN connections will be closed each time the master/slave handover happens. This means that remote users that have connected to the SSLVPN will be disconnected and can simply reconnect. This master/slave swap happens twice in the space of a few minutes, so they may be disconnected twice. All in all the upgrade takes about five minutes to complete.
Remember, as with all upgrades ensure that you have:
- A copy of the old config
- The old firmware image you are upgrading from
- Have feet on the ground in-case anything goes pear shaped
- Have READ THE RELEASE NOTES before upgrading! ;)




No comments:
Post a Comment